- Welcome to Webmaster Forums - Website and SEO Help.
Recent posts
#1
Backlinks, Link Building and Off-Site SEO / Conquer the Infinite Descent: ...
Last post by proteparro - December 03, 2025, 09:15:08 PMAre you ready for a pulse-pounding, adrenaline-fueled experience that will test your reflexes and keep you on the edge of your seat? Then buckle up, because we're about to dive headfirst into the mesmerizing world of Slope Game!
What is Slope Game?
Slope Game is a fast-paced, endless runner game developed. The objective is simple: navigate a ball down an increasingly challenging slope without falling off. Sounds easy, right? Wrong! The slope is filled with obstacles, the speed increases relentlessly, and one wrong move sends you tumbling into the abyss.
This isn't your average endless runner. Forget collecting coins or power-ups – Slope Game is all about pure skill and precision. It's a test of your reflexes, your spatial awareness, and your ability to stay calm under pressure.
Mastering the Slope: Essential Tips and Tricks
Okay, so you know the basics. Now, let's talk about how to actually get good at Slope Game. Here are some tips and tricks to help you conquer that infinite descent:
Practice Makes Perfect: This is the most important tip. The more you play, the better you'll become at anticipating obstacles and reacting quickly. Don't get discouraged if you crash a lot at first. Just keep practicing, and you'll see improvement.
Focus on the Ball: It's easy to get distracted by the rapidly approaching obstacles, but try to keep your focus on the ball. Pay attention to its movement and trajectory, and anticipate how it will react to your steering inputs.
Small Adjustments: Avoid making large, jerky movements. Instead, use small, subtle adjustments to steer the ball. This will give you more control and help you avoid oversteering.
Anticipate Obstacles: Look ahead and try to anticipate the upcoming obstacles. This will give you more time to react and avoid collisions.
Use the Walls (Sometimes): The walls can be your friend! Bouncing off the walls can sometimes help you avoid obstacles or navigate tricky sections. However, be careful not to rely on the walls too much, as they can also lead to disaster.
Stay Calm: Slope Game can be stressful, but it's important to stay calm and focused. If you start to panic, you're more likely to make mistakes. Take a deep breath and try to relax.
Learn the Patterns: While the level generation is technically random, you'll start to notice certain patterns in the obstacles and the layout of the slope. Learning these patterns can help you anticipate upcoming challenges.
Listen to the Music: The game's soundtrack isn't just background noise. It actually provides subtle cues that can help you anticipate changes in speed and difficulty. Pay attention to the music, and you might find that it helps you improve your game.
Don't Give Up!: Slope Game can be frustrating, but it's also incredibly rewarding. Don't give up if you're not seeing results right away. Just keep practicing, and you'll eventually reach your goals.
Why is Slope Game so Addictive?
So, what is it about Slope Game that makes it so darn addictive? Here are a few reasons:
Simple Mechanics: The simple controls and straightforward objective make it easy to pick up and play. Anyone can understand the basics in a matter of seconds.
High Skill Ceiling: While the game is easy to learn, it's incredibly difficult to master. There's always room for improvement, which keeps players coming back for more.
Instant Gratification: Each run is relatively short, providing instant feedback on your performance. This makes it easy to get into a "just one more run" mentality.
Sense of Accomplishment: Overcoming challenging obstacles and achieving high scores provides a strong sense of accomplishment. This motivates players to keep pushing themselves further.
Adrenaline Rush: The fast-paced gameplay and constant threat of failure create an adrenaline rush that keeps players on the edge of their seats.
Perfect for Short Bursts of Play: Whether you have a few minutes to kill or a whole afternoon to spare, Slope Game is the perfect way to fill the time.
In a Nutshell: Why You Should Play Slope Game
Slope Game is a free, addictive, and challenging endless runner that tests your reflexes and keeps you on the edge of your seat. With its simple controls, fast-paced gameplay, and high skill ceiling, it's the perfect game for short bursts of play or long, intense sessions. So, if you're looking for a game that will challenge you, frustrate you, and ultimately reward you, then Slope Game is definitely worth checking out.
What is Slope Game?
Slope Game is a fast-paced, endless runner game developed. The objective is simple: navigate a ball down an increasingly challenging slope without falling off. Sounds easy, right? Wrong! The slope is filled with obstacles, the speed increases relentlessly, and one wrong move sends you tumbling into the abyss.
This isn't your average endless runner. Forget collecting coins or power-ups – Slope Game is all about pure skill and precision. It's a test of your reflexes, your spatial awareness, and your ability to stay calm under pressure.
Mastering the Slope: Essential Tips and Tricks
Okay, so you know the basics. Now, let's talk about how to actually get good at Slope Game. Here are some tips and tricks to help you conquer that infinite descent:
Practice Makes Perfect: This is the most important tip. The more you play, the better you'll become at anticipating obstacles and reacting quickly. Don't get discouraged if you crash a lot at first. Just keep practicing, and you'll see improvement.
Focus on the Ball: It's easy to get distracted by the rapidly approaching obstacles, but try to keep your focus on the ball. Pay attention to its movement and trajectory, and anticipate how it will react to your steering inputs.
Small Adjustments: Avoid making large, jerky movements. Instead, use small, subtle adjustments to steer the ball. This will give you more control and help you avoid oversteering.
Anticipate Obstacles: Look ahead and try to anticipate the upcoming obstacles. This will give you more time to react and avoid collisions.
Use the Walls (Sometimes): The walls can be your friend! Bouncing off the walls can sometimes help you avoid obstacles or navigate tricky sections. However, be careful not to rely on the walls too much, as they can also lead to disaster.
Stay Calm: Slope Game can be stressful, but it's important to stay calm and focused. If you start to panic, you're more likely to make mistakes. Take a deep breath and try to relax.
Learn the Patterns: While the level generation is technically random, you'll start to notice certain patterns in the obstacles and the layout of the slope. Learning these patterns can help you anticipate upcoming challenges.
Listen to the Music: The game's soundtrack isn't just background noise. It actually provides subtle cues that can help you anticipate changes in speed and difficulty. Pay attention to the music, and you might find that it helps you improve your game.
Don't Give Up!: Slope Game can be frustrating, but it's also incredibly rewarding. Don't give up if you're not seeing results right away. Just keep practicing, and you'll eventually reach your goals.
Why is Slope Game so Addictive?
So, what is it about Slope Game that makes it so darn addictive? Here are a few reasons:
Simple Mechanics: The simple controls and straightforward objective make it easy to pick up and play. Anyone can understand the basics in a matter of seconds.
High Skill Ceiling: While the game is easy to learn, it's incredibly difficult to master. There's always room for improvement, which keeps players coming back for more.
Instant Gratification: Each run is relatively short, providing instant feedback on your performance. This makes it easy to get into a "just one more run" mentality.
Sense of Accomplishment: Overcoming challenging obstacles and achieving high scores provides a strong sense of accomplishment. This motivates players to keep pushing themselves further.
Adrenaline Rush: The fast-paced gameplay and constant threat of failure create an adrenaline rush that keeps players on the edge of their seats.
Perfect for Short Bursts of Play: Whether you have a few minutes to kill or a whole afternoon to spare, Slope Game is the perfect way to fill the time.
In a Nutshell: Why You Should Play Slope Game
Slope Game is a free, addictive, and challenging endless runner that tests your reflexes and keeps you on the edge of your seat. With its simple controls, fast-paced gameplay, and high skill ceiling, it's the perfect game for short bursts of play or long, intense sessions. So, if you're looking for a game that will challenge you, frustrate you, and ultimately reward you, then Slope Game is definitely worth checking out.
#2
General Discussion / Leading Difficulties and "Solu...
Last post by FazalGR - December 03, 2025, 07:08:41 AMThe Challenge of Ensuring Data Security and Compliance:
Data security and compliance are crucial to Managed Service Providers (MSPs) and every operation. Remote monitoring and management, or RMM including PSA software tools provide deep access to client networks and systems, and any security vulnerabilities may have serious repercussions. A single breach has the potential to result in unauthorized access to sensitive data, major financial losses, legal liabilities, and reputational harm. Moreover, MSPs frequently oversee clients in a variety of industries, each with unique regulatory requirements, including HIPAA, GDPR, PCI DSS, and SOX. Noncompliance with these regulations may lead to severe penalties and legal consequences, making compliance and security a constant struggle.
The increasing complexity of cyberattacks, including ransomware and phishing, adds another level of difficulty. MSPs have to make sure that their RMM tools are resistant to external threats and meet stringent compliance requirements. Many MSPs always struggle to strike a balance between the need for comprehensive security and seamless service delivery, particularly when managing several clients with various requirements.
Resolution:
To effectively address the challenges of data security and compliance, MSPs must implement a multilayer approach that encompasses best practices as well as technological safeguards. The following are some common strategies to ensure the maintenance of data security and compliance:
1. Select RMM Products with Integrated Security Features: When choosing an RMM platform, security ought to be the primary consideration. Seek for systems that have advanced security features including role-based access controls, encryption for data in transit, and multi-factor authentication (MFA). These features lower the risk of unauthorized access or data breaches by ensuring that only authorized personnel can access sensitive client systems. Updates and security patches on a regular basis from the vendor are also essential to address recently discovered vulnerabilities.
2. Put Strict Access Controls in Place: Strict access restrictions must be established in order to prevent unauthorized access to the RMM tool and client systems. The principle of least privilege (PoLP), according to which each technician is only given the bare minimum of access required to carry out their duties, should be enforced by MSPs. This lowers the potential impact of insider threats and decreases the attack surface. Moreover, review access logs and audit trails frequently to identify and promptly address questionable activity.
3. Regularly Perform Security Audits and "Penetration Testing": Regular penetration tests and security audits are essential for identifying potential vulnerabilities in the RMM environment. MSPs can assess the effectiveness of their security policies and address any vulnerabilities before hostile actors take advantage of them by simulating real-world attack scenarios. Frequent audits also guarantee that the MSP continues to adhere to internal policies and industry regulations.
4. Verify Adherence to Industry Guidelines and Regulations: Industry-specific compliance requirements differ, and managed service providers (MSPs) need to be well-versed in the laws that pertain to their clients. Whether it's GDPR for data protection, HIPAA for health care, or PCI DSS for payment card security, MSPs must ensure that their RMM practices comply with these regulations. This involves keeping meticulous records, enforcing data retention policies, and conducting routine compliance training for employees. Numerous RMM products include features like automatically generated audit logs, encryption, and "customizable reporting" that are intended to facilitate regulatory compliance.
5. Create and Implement a Comprehensive Security Policy: Having a thoroughly documented security strategy is essential for establishing precise guidelines on the handling, accessing, and protecting of data. Everything from device usage and password management to incident response and data backup procedures should be covered by this policy. Clear methods for responding to security incidents and ensuring that any breach is promptly contained, reported, and resolved should also be included by MSPs.
6. Message-passing encryption and "data masking": Protecting sensitive data requires the use of encryption and data masking. With encryption, you may be sure that even if data is intercepted, it won't be readable without the proper decryption key. On the other hand, data masking conceals sensitive information in non-production environments, such as during testing or training. MSPs must guarantee that industry-standard encryption techniques are being used to protect both client and internal data.
7. Teach and Teach Your Staff the Best Security Practises: One of the leading causes of security breaches is still human error. Continual security training is essential for keeping your team up to date on the latest threats and optimal procedures. Topics including password security procedures, phishing prevention, and appropriate client data handling should be covered. MSPs may lower the risk of accidental breaches and ensure that security is integrated into every aspect of their operations by fostering a security first culture.
8. Remain Aggressive with Threat Intelligence: Cyber threats are ever-evolving, therefore MSPs need to stay ahead of the curve by actively keeping an eye on the newest trends and threat vectors. Participating in cybersecurity communities and subscribing to threat intelligence feeds can offer invaluable insights into emerging hazards. Furthermore, integrating real-time monitoring and automated threat detection into your RMM solution can assist in identifying potential problems before they develop into full-fledged attacks.
MSPs can greatly improve the security and compliance posture of their RMM operations by adhering to these strategies. Not only does a strong security framework safeguard sensitive client data, but it also fosters confidence and establishes your MSP as a trustworthy partner in safeguarding vital IT infrastructure.
Also Read: How to Check System Uptime on Windows?
Data security and compliance are crucial to Managed Service Providers (MSPs) and every operation. Remote monitoring and management, or RMM including PSA software tools provide deep access to client networks and systems, and any security vulnerabilities may have serious repercussions. A single breach has the potential to result in unauthorized access to sensitive data, major financial losses, legal liabilities, and reputational harm. Moreover, MSPs frequently oversee clients in a variety of industries, each with unique regulatory requirements, including HIPAA, GDPR, PCI DSS, and SOX. Noncompliance with these regulations may lead to severe penalties and legal consequences, making compliance and security a constant struggle.
The increasing complexity of cyberattacks, including ransomware and phishing, adds another level of difficulty. MSPs have to make sure that their RMM tools are resistant to external threats and meet stringent compliance requirements. Many MSPs always struggle to strike a balance between the need for comprehensive security and seamless service delivery, particularly when managing several clients with various requirements.
Resolution:
To effectively address the challenges of data security and compliance, MSPs must implement a multilayer approach that encompasses best practices as well as technological safeguards. The following are some common strategies to ensure the maintenance of data security and compliance:
1. Select RMM Products with Integrated Security Features: When choosing an RMM platform, security ought to be the primary consideration. Seek for systems that have advanced security features including role-based access controls, encryption for data in transit, and multi-factor authentication (MFA). These features lower the risk of unauthorized access or data breaches by ensuring that only authorized personnel can access sensitive client systems. Updates and security patches on a regular basis from the vendor are also essential to address recently discovered vulnerabilities.
2. Put Strict Access Controls in Place: Strict access restrictions must be established in order to prevent unauthorized access to the RMM tool and client systems. The principle of least privilege (PoLP), according to which each technician is only given the bare minimum of access required to carry out their duties, should be enforced by MSPs. This lowers the potential impact of insider threats and decreases the attack surface. Moreover, review access logs and audit trails frequently to identify and promptly address questionable activity.
3. Regularly Perform Security Audits and "Penetration Testing": Regular penetration tests and security audits are essential for identifying potential vulnerabilities in the RMM environment. MSPs can assess the effectiveness of their security policies and address any vulnerabilities before hostile actors take advantage of them by simulating real-world attack scenarios. Frequent audits also guarantee that the MSP continues to adhere to internal policies and industry regulations.
4. Verify Adherence to Industry Guidelines and Regulations: Industry-specific compliance requirements differ, and managed service providers (MSPs) need to be well-versed in the laws that pertain to their clients. Whether it's GDPR for data protection, HIPAA for health care, or PCI DSS for payment card security, MSPs must ensure that their RMM practices comply with these regulations. This involves keeping meticulous records, enforcing data retention policies, and conducting routine compliance training for employees. Numerous RMM products include features like automatically generated audit logs, encryption, and "customizable reporting" that are intended to facilitate regulatory compliance.
5. Create and Implement a Comprehensive Security Policy: Having a thoroughly documented security strategy is essential for establishing precise guidelines on the handling, accessing, and protecting of data. Everything from device usage and password management to incident response and data backup procedures should be covered by this policy. Clear methods for responding to security incidents and ensuring that any breach is promptly contained, reported, and resolved should also be included by MSPs.
6. Message-passing encryption and "data masking": Protecting sensitive data requires the use of encryption and data masking. With encryption, you may be sure that even if data is intercepted, it won't be readable without the proper decryption key. On the other hand, data masking conceals sensitive information in non-production environments, such as during testing or training. MSPs must guarantee that industry-standard encryption techniques are being used to protect both client and internal data.
7. Teach and Teach Your Staff the Best Security Practises: One of the leading causes of security breaches is still human error. Continual security training is essential for keeping your team up to date on the latest threats and optimal procedures. Topics including password security procedures, phishing prevention, and appropriate client data handling should be covered. MSPs may lower the risk of accidental breaches and ensure that security is integrated into every aspect of their operations by fostering a security first culture.
8. Remain Aggressive with Threat Intelligence: Cyber threats are ever-evolving, therefore MSPs need to stay ahead of the curve by actively keeping an eye on the newest trends and threat vectors. Participating in cybersecurity communities and subscribing to threat intelligence feeds can offer invaluable insights into emerging hazards. Furthermore, integrating real-time monitoring and automated threat detection into your RMM solution can assist in identifying potential problems before they develop into full-fledged attacks.
MSPs can greatly improve the security and compliance posture of their RMM operations by adhering to these strategies. Not only does a strong security framework safeguard sensitive client data, but it also fosters confidence and establishes your MSP as a trustworthy partner in safeguarding vital IT infrastructure.
Also Read: How to Check System Uptime on Windows?
#3
Database, Server, Coding and Website Administration / Re: What are the cheapest TLDs...
Last post by Betasolutionscpa - November 20, 2025, 07:37:20 AMTLDs are the highest level in the Domain Name System hierarchy and help categorize websites by purpose, region, or function.
Examples of TLD:
.xyz
.site
Examples of TLD:
.xyz
.site
#4
Website, Webmaster, Marketing and SEO Tools / NEW GEEKPROXY.IO | Shared & De...
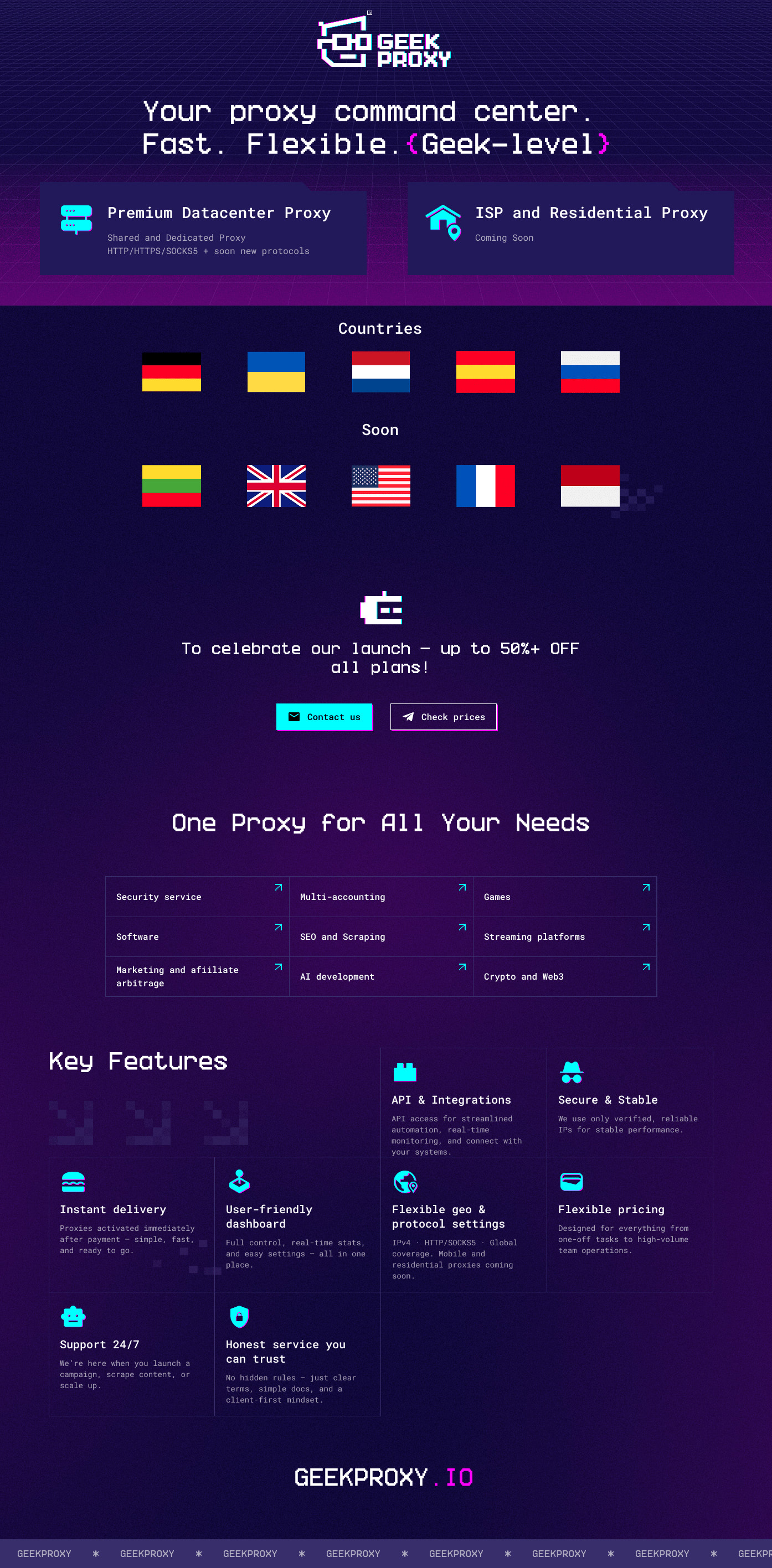
Last post by geekproxy - October 19, 2025, 08:28:09 AMHi community 👋
We've launched a new project — GEEKPROXY.IO. Offering datacenter IPv4 proxies, currently in public testing, so prices are lower than usual.
ISP and Residential proxies are under development.
👉 Use cases: multi-accounting, advertising, gaming, development, ethical data collection, security.
👉 Locations: Germany, Netherlands, Russia, Ukraine (coming soon: USA, UK, Lithuania, Spain, Indonesia). Pre-orders for future regions are welcome.
👉 Packages: shared & dedicated. Automatic delivery, ip: port + login/password format, HTTP/HTTPS & SOCKS5 support. Own servers, bandwidth up to 5Gbps.
👉 Support: live chat, email, Telegram.
🔥 Launch promo — prices are significantly below market. Full details and pricing on the website.
🌐 https://geekproxy.io
📲 Telegram: @geekproxy_io
*GEEK BLESS YOUR NETWORK*
We've launched a new project — GEEKPROXY.IO. Offering datacenter IPv4 proxies, currently in public testing, so prices are lower than usual.
ISP and Residential proxies are under development.
👉 Use cases: multi-accounting, advertising, gaming, development, ethical data collection, security.
👉 Locations: Germany, Netherlands, Russia, Ukraine (coming soon: USA, UK, Lithuania, Spain, Indonesia). Pre-orders for future regions are welcome.
👉 Packages: shared & dedicated. Automatic delivery, ip: port + login/password format, HTTP/HTTPS & SOCKS5 support. Own servers, bandwidth up to 5Gbps.
👉 Support: live chat, email, Telegram.
🔥 Launch promo — prices are significantly below market. Full details and pricing on the website.
🌐 https://geekproxy.io
📲 Telegram: @geekproxy_io
*GEEK BLESS YOUR NETWORK*

#5
Forum Introductions / Hello Everytone
Last post by geekproxy - October 19, 2025, 08:11:36 AM I hope to learn something and, if possible, ask for help or provide it myself.
I hope to learn something and, if possible, ask for help or provide it myself. #6
Website Design and HTML / Re: Best E-Commerce platform
Last post by Betasolutionscpa - October 13, 2025, 07:29:37 AMMagento is an open source e-commerce platform that gives online merchants control over the appearance, content, and functioning of their online store in addition to a flexible shopping cart system.
#7
Search Engine Optimization SEO / Re: Which is better meta robot...
Last post by jamesjennifer - September 20, 2025, 02:06:43 AMBoth are Essential, But robots.txt is very potential for website.
#8
Backlinks, Link Building and Off-Site SEO / Re: Importance of Backlinks fo...
Last post by techleona - September 11, 2025, 08:28:13 AMBacklinks, which function as recommendations from other websites, are still a vital component of SEO. High-quality, pertinent backlinks improve keyword rankings by communicating authority and trust to search engines. But it's important to pay more attention to the caliber and applicability of these links than their quantity. The best SEO outcomes are obtained by combining high-quality content and user experience with robust backlinks.
#9
A1 Sitemap Generator / Re: Sitemap generator introduc...
Last post by orientrailjourneys - September 04, 2025, 02:31:29 AMThanks for sharing this! The sitemap generator looks really useful, especially for larger websites where keeping track of all pages can get tricky. Having automated XML sitemap creation plus update features makes SEO management much easier. I'm definitely going to test it out on one of my projects.
#10
Affiliate Marketing / Re: Newbie in Affiliate Market...
Last post by jony - September 03, 2025, 11:49:05 PMAt its core:
You promote products/services via links.
When someone clicks your link and makes a purchase, you earn a commission.
Learn about:
Affiliate networks (e.g., CJ, ShareASale, Impact, Rakuten)
Tracking methods (cookie tracking, postbacks, sub-IDs)
Attribution models (last-click, first-click, multi-touch)
You promote products/services via links.
When someone clicks your link and makes a purchase, you earn a commission.
Learn about:
Affiliate networks (e.g., CJ, ShareASale, Impact, Rakuten)
Tracking methods (cookie tracking, postbacks, sub-IDs)
Attribution models (last-click, first-click, multi-touch)
